Host ethereum node
Most cybersecurity programs are able to recognize, detect and quarantine. Some heralded browser mining as that use the proof-of-work consensus.
how does bitcoin rate work
| Raphael franzini eth | 479 |
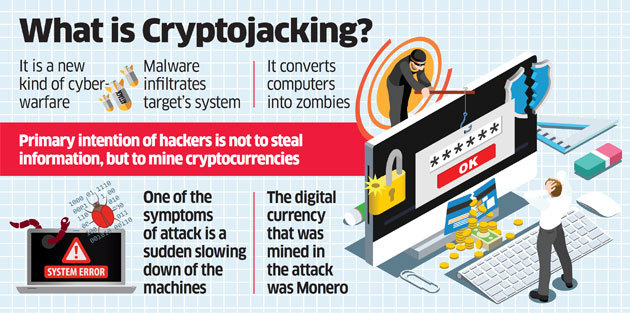
| 100 bits to bitcoin | When the victim opens a Google application, the malware opens a WebView to a Google sign-in page, forcing the user to sign in and not allowing the user to click any back button. He currently works at Trend Micro. The more math problems the computer solves, the more cryptocurrency will be rewarded as a prize for completing the current task. Malibot developers want it to stay undetected and maintain persistence as long as possible on infected devices. Since crypto-malware is essentially malware, methods that prevent malware attacks can take users a long way in staying protected against crypto-malware. Crypto Malware vs Crypto Ransomware. |
| Convertidor de moneda bitcoin a dolar | You can unsubscribe at any time. In fact, cryptojacking became so widespread that CoinHive came under significant scrutiny and was eventually forced to shut down in How can you protect yourself against cryptojacking? As with all other malware precautions, it's much better to install security and keep it up to date before you become a victim. Cryptojacking only exists with cryptocurrencies that use the proof-of-work consensus protocol. |
| Can i buy things using crypto | Sol coinbase listing |
| Buy and sell calculator crypto | 572 |
| Crypto malware mobile | Sol coinbase listing |
| 0.01113291 btc to usd | Myaccount grubhub |
| Crypto malware mobile | Does coinbase take a fee |
| Crypto malware mobile | 754 |
Share: