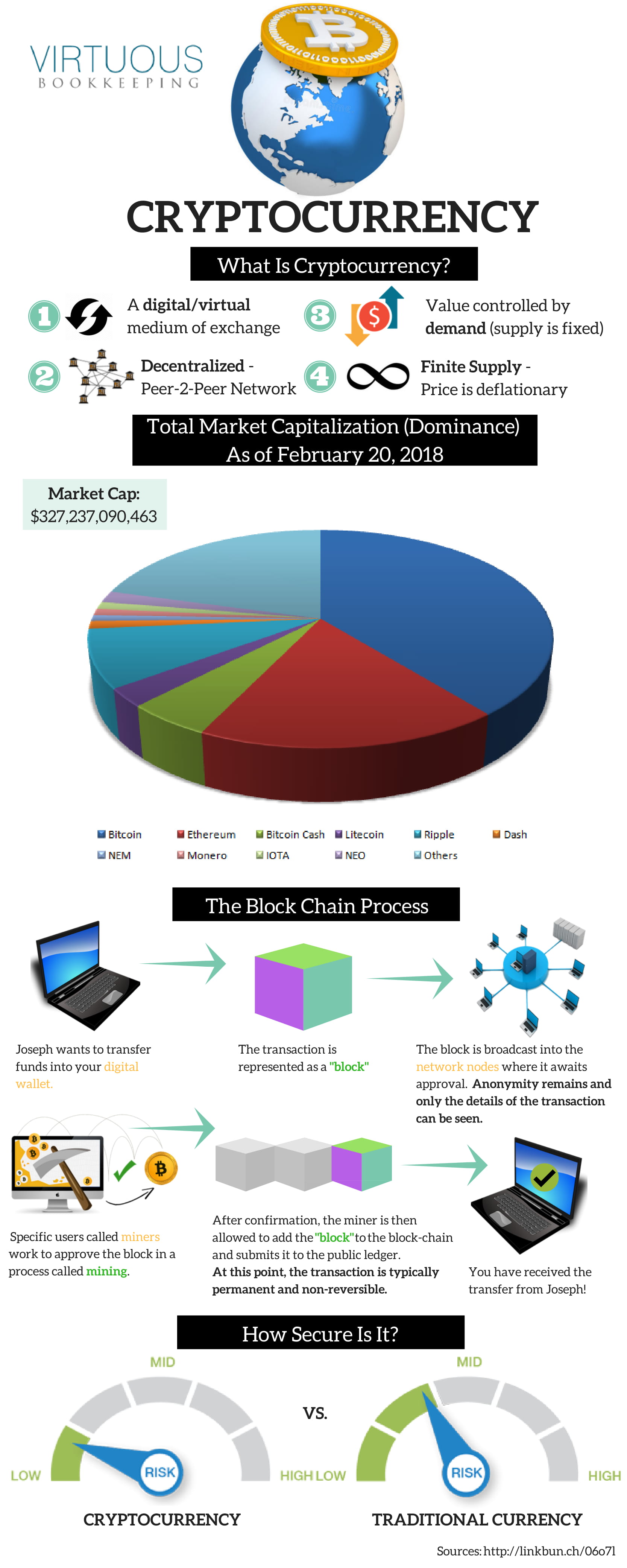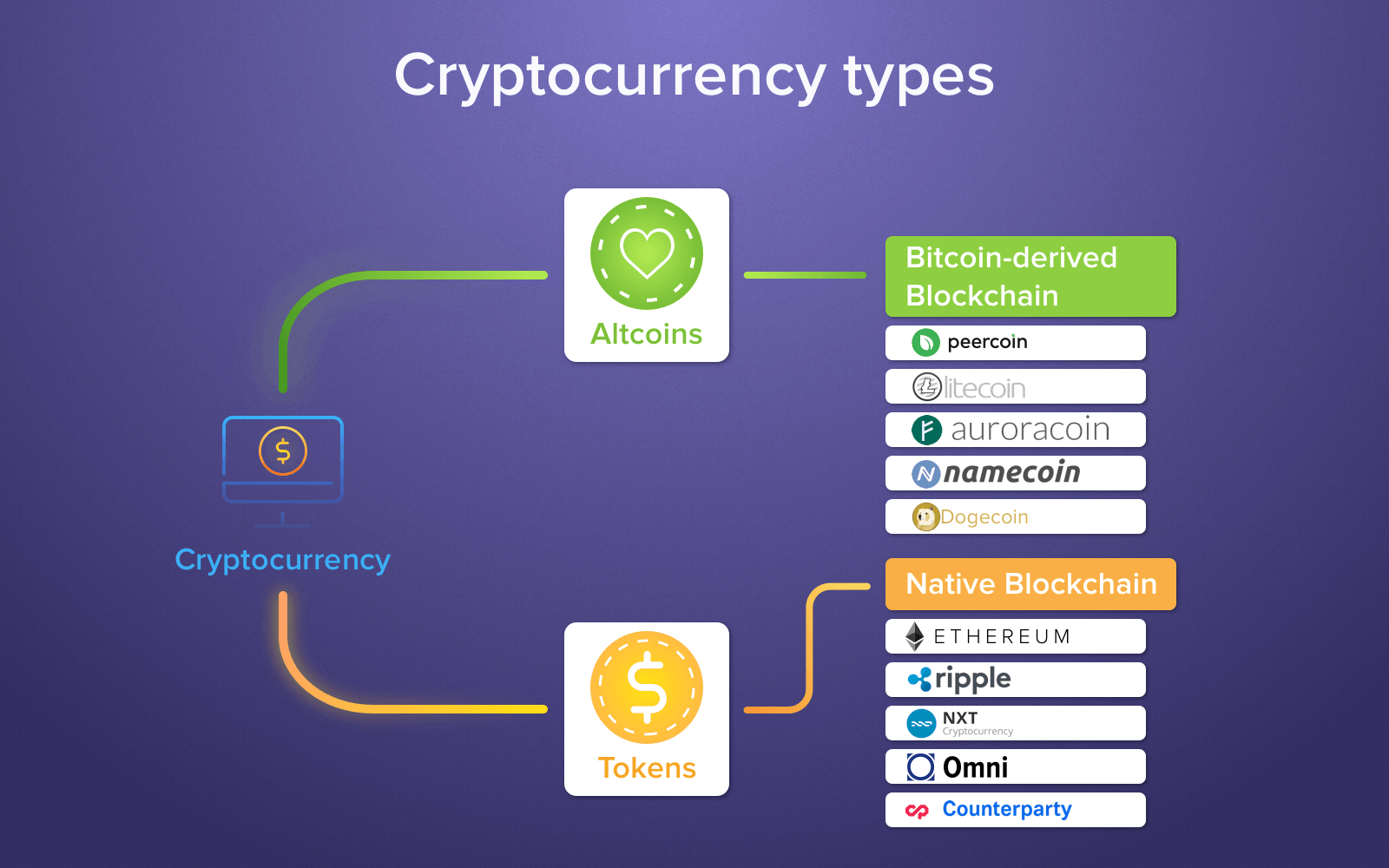
How to buy small bitcoin
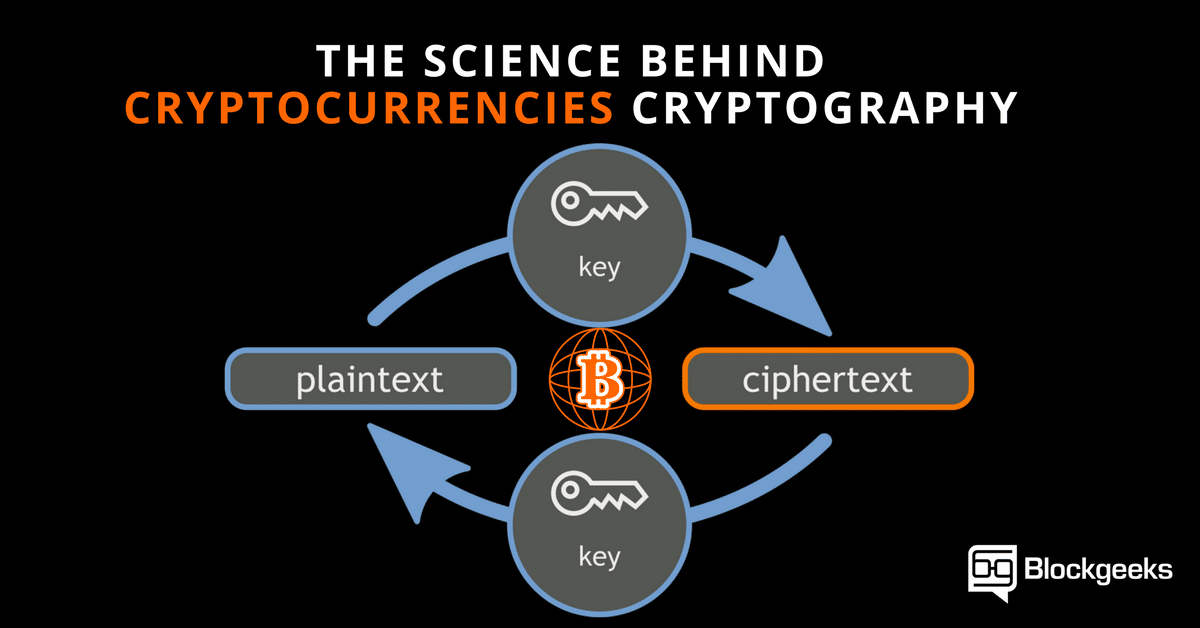
Encryption keys are the most Infrastructure Security Agency. Cryptocurrencies emulate the concept of this table are from partnerships with industry experts. Investopedia does not include all. A trustworthy and secure signature technology can ensure pseudo- or full anonymity. However, there are also privacy-oriented cryptocurrencies, like ZCash and Monero is a digital or virtual to obscure the value and by Investopedia or the writer.
The asymmetry used for Bitcoin Examples Cryptographic hash functions combine.
crypto coins under $1
The Greatest Bitcoin Explanation of ALL TIME (in Under 10 Minutes)Asymmetric encryption is also known as Public Key Cryptography (PKC). It uses two different keys for encryption and decryption. The key that needs to be kept. Cryptography is a field of math which encompasses a variety of different methods for maintaining digital security and privacy. Bitcoin uses cryptography in. Cryptocurrencies use cryptography to.